Summary
-
BanHammer-ng: blocking bad guys on Mozilla network

- Brozilla: Intrusion Detection with Bro at Mozilla
Anthony Verez, @netantho averez@mozilla.com

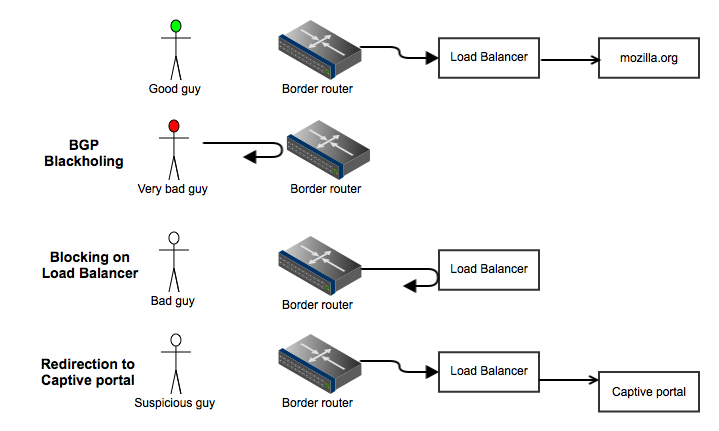
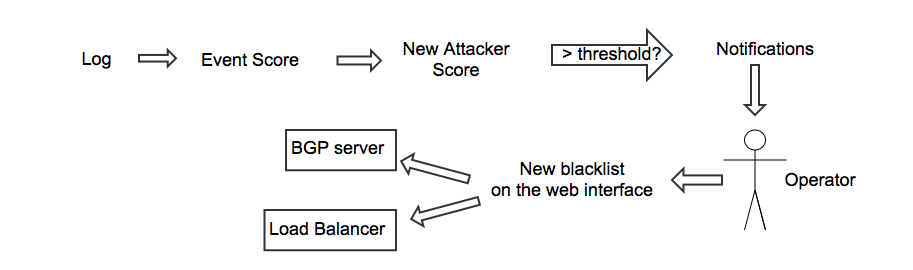
alert any any -> any any
(flags: SF,12; msg: "Possible SYN FIN scan";)